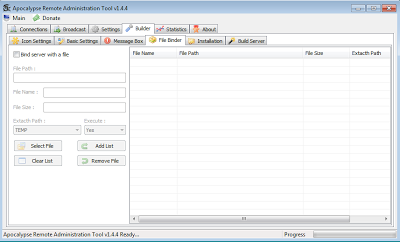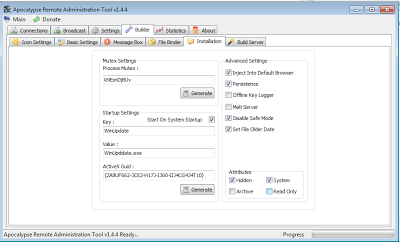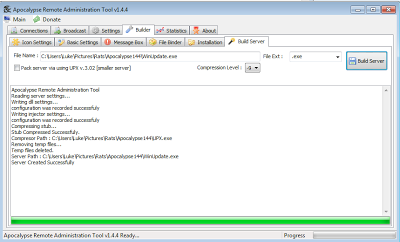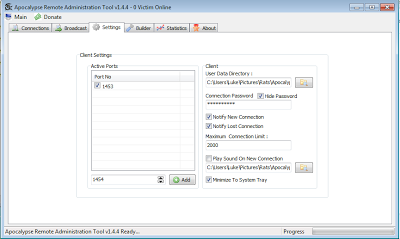
Platform: Windows 8 x64
Compilation Date: 26.03.2013
Based on Edition: Pro
Automated Installation : Yes
Category : Operating System
Activation Needed :No
Kernel Type: Hybrid
Installation Type: BIOS
Digitally Signed for Security : Yes
UEFI Support: Enabled
CD-Key : N/A
Size: 4.3 GB
No of DVD's: 1 (Normal DVD)
Format: ISO Image File
Installation Time : 25 - 30 Mins
Author: Nishant (Reckons International Team)
For Assistance :
Code
http://www.reckonsteam.com
Minimum System Requirements:
В· 1 GB RAM (Recommended 2GB RAM)
В· 20 GB of HDD space
В· 128 MB of Graphics Memory (Capable to run Windows Aero)
· 17’ inch Monitor (1024 x 76
В· DVD-ROM or DVD-RAM
В· Pixel Shader 2.0
В· Dual Core Processors
Compilation Date: 26.03.2013
Based on Edition: Pro
Automated Installation : Yes
Category : Operating System
Activation Needed :No
Kernel Type: Hybrid
Installation Type: BIOS
Digitally Signed for Security : Yes
UEFI Support: Enabled
CD-Key : N/A
Size: 4.3 GB
No of DVD's: 1 (Normal DVD)
Format: ISO Image File
Installation Time : 25 - 30 Mins
Author: Nishant (Reckons International Team)
For Assistance :
Code
http://www.reckonsteam.com
Minimum System Requirements:
В· 1 GB RAM (Recommended 2GB RAM)
В· 20 GB of HDD space
В· 128 MB of Graphics Memory (Capable to run Windows Aero)
· 17’ inch Monitor (1024 x 76
В· DVD-ROM or DVD-RAM
В· Pixel Shader 2.0
В· Dual Core Processors
1.) 7-Zip
2.) WinRAR
3.) CDBurnerXP
4.) Mozilla Firefox
5.) K-Lite Mega Codec Package
6.) Adobe Flash Player
7.) Notepad ++
8.) Internet Download Manager
9.) Java Runtime Environment
10.) CCleaner Bussines Edition
11.) RocketDock
12.) VLC Media Player
14.) TuneUp Utilities 2013
17.) MalwareBytes Anti-Malware
18.) StartIsBack
2.) WinRAR
3.) CDBurnerXP
4.) Mozilla Firefox
5.) K-Lite Mega Codec Package
6.) Adobe Flash Player
7.) Notepad ++
8.) Internet Download Manager
9.) Java Runtime Environment
10.) CCleaner Bussines Edition
11.) RocketDock
12.) VLC Media Player
14.) TuneUp Utilities 2013
17.) MalwareBytes Anti-Malware
18.) StartIsBack